Hijacked Discord Invites: The New Lure in Phishing Campaigns
Introduction
In a concerning development for the security of social platforms and their users, attackers are now exploiting Discord invite links as a novel vector for phishing and malware distribution. This tactic represents a dangerous blend of social engineering and technical exploitation that can deceive even experienced users. The attack surfaced in a report by The Hacker News on June 17, 2025, highlighting how these malicious campaigns hijack trust by misusing Discord’s legitimate infrastructure.
How the Attack Works
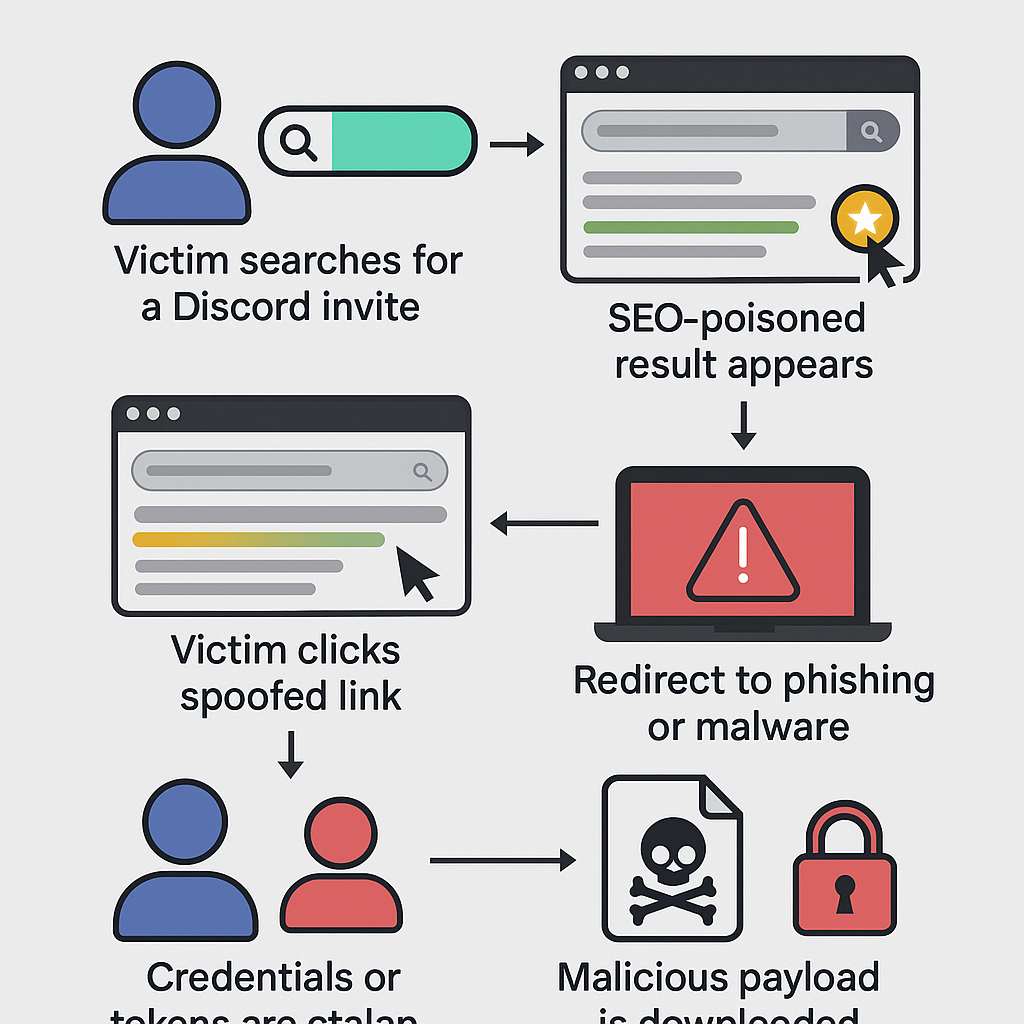
At the core of this campaign is Discord’s invite system. Normally, these links (discord.gg/xyz) are generated by server admins to onboard new users. However, attackers have discovered a method to hijack these links, pointing them to fake landing pages that mimic legitimate Discord content but are instead controlled by the attacker.
1. Spoofed Landing Pages
The fake invite links redirect victims to phishing sites that visually replicate Discord’s invite screen. Users are prompted to “Join Server,” but in reality, these sites serve malware-laced payloads or harvest credentials.
2. SEO Poisoning
To increase visibility and trust, attackers use SEO techniques to make these hijacked links appear in Google Search results for specific Discord communities or NFT/gaming groups. This ensures organic reach, drawing in users who are actively searching for the real servers.
3. Redirection to Malware
Upon clicking the spoofed invite, users are often redirected to:
- .exe downloads posing as Discord installers
- Fake giveaways or NFT drops
- Credential harvesting forms asking for Discord login or email credentials
Real-World Example
The article highlights a particular case where users searching for a popular gaming Discord server landed on a hijacked link. Instead of joining the server, they were redirected to a page that prompted them to download a malicious file disguised as a “Discord verification” tool. The file deployed information-stealing malware on execution, targeting browser cookies, Discord tokens, and saved passwords.
Technical Breakdown
- Domain Spoofing: Attackers registered domains resembling legitimate Discord or community URLs (e.g.,
discords-giveaway.com,discord.gg.login-secure.com). - Link Cloaking: Shortened URLs (e.g.,
bit.ly,tinyurl) hide the true destination. - Payload Delivery: Malware such as RedLine Stealer, RATs, and browser hijackers were commonly delivered.
- Token Grabbers: JavaScript was used in some cases to harvest Discord tokens directly from localStorage or the
leveldbdirectory.
Why It Works
This method is particularly effective because:
- Users trust the Discord brand
- Invite links look legitimate
- No immediate signs of compromise appear
- Users are often distracted by the lure (NFT drop, giveaway, invite-only access)
Mitigation & Protection
For Users:
- Double-check links: Always verify the full URL before clicking. Look out for extra domains or misspellings.
- Avoid third-party sites: Only join Discord servers via official websites or known communities.
- Use browser isolation or sandboxes when interacting with unknown links.
- Enable 2FA on Discord to protect your account even if credentials are stolen.
For Server Admins:
- Monitor for clones: Search for lookalike domains mimicking your community.
- Report phishing sites: Use services like Google Safe Browsing or Discord’s abuse portal.
- Educate your users: Share awareness guides on your server.
For Security Teams:
- Add Discord invite domains to watchlists
- Use DNS filtering and threat intel tools to detect malicious redirects
- Monitor employee devices for suspicious Discord token activity
Implications for the Future
This campaign is a wake-up call for platform security. It shows how trust can be weaponized through very subtle infrastructure manipulation. Discord, known for its developer-friendly APIs and widespread use among gamers and professionals alike, is now part of a broader attack surface. If attackers can continue to abuse invite-based ecosystems, other platforms like Slack, Telegram, and Microsoft Teams may also see similar exploitation.
Final Thoughts
As phishing tactics evolve, attackers are moving beyond fake login pages and into ecosystem manipulation. The hijacking of Discord invites marks a shift in adversarial strategy—where the infrastructure of trust becomes the attack vector itself. Users, communities, and security teams must respond by raising awareness, monitoring DNS and SEO vectors, and enforcing zero-trust link policies.
Source: https://thehackernews.com/2025/06/discord-invite-link-hijacking-delivers.html
