The Most Common Network Port Attacks – And How to Defend Against Them

When it comes to cybersecurity, attackers rarely go in blind. They systematically scan for open ports—the digital doors and windows into your network. Some ports are more popular targets than others, simply because of the critical services running behind them. In this article, we break down the typical attacks seen on the most common ports and provide actionable defense strategies to help keep your systems secure.
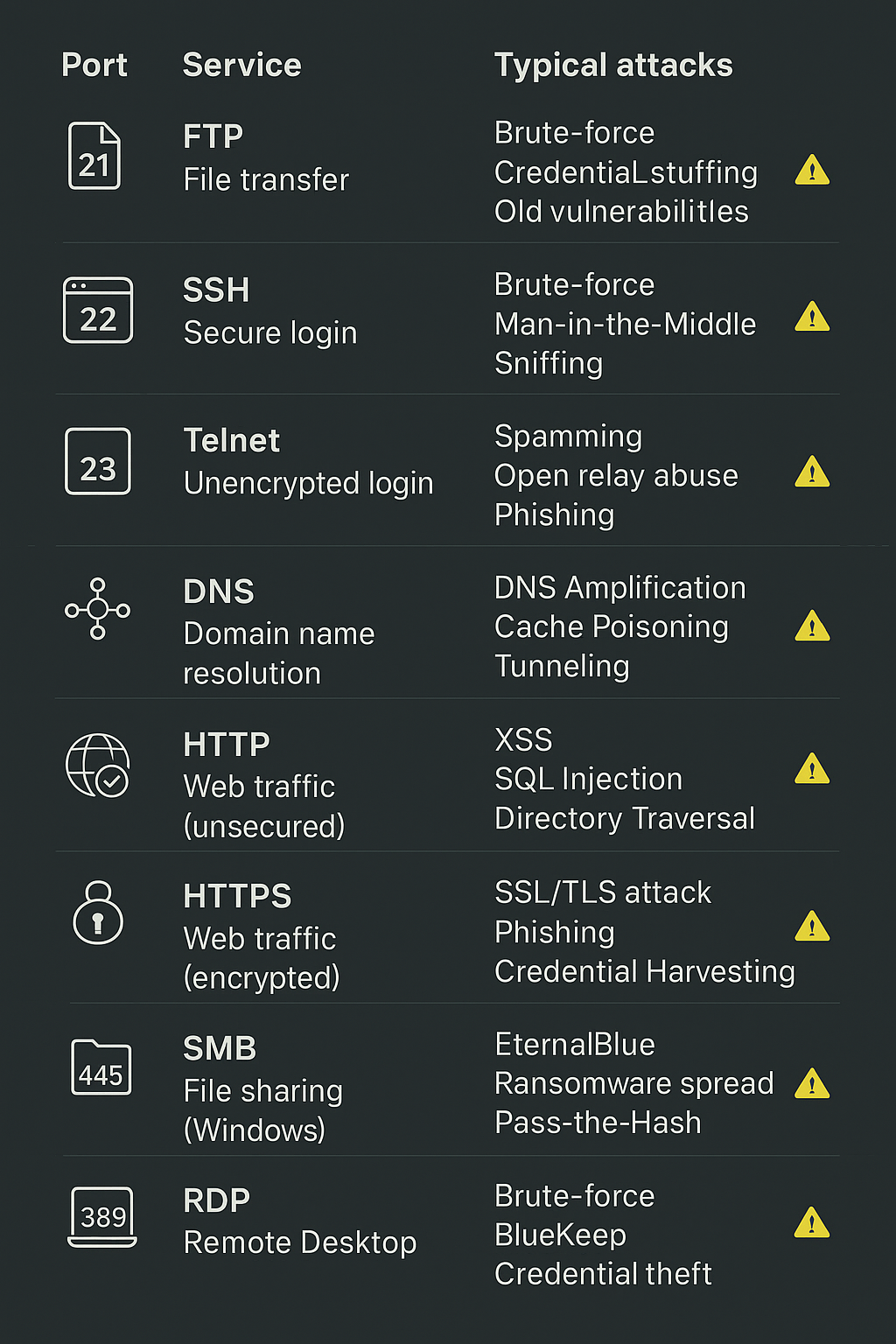
1. FTP (Port 21) – File Transfer Protocol
Attacks:
- Brute-force & Anonymous Login: Attackers attempt to guess passwords or exploit misconfigurations allowing “anonymous” access, gaining entry without credentials.
- Directory Traversal: Malicious actors manipulate file paths to access directories and files outside the permitted scope, sometimes leading to full system compromise.
Defense:
- Disable anonymous access unless absolutely necessary.
- Enforce strong, unique passwords and limit failed login attempts.
- Restrict FTP access to trusted IP addresses or internal networks.
- Replace plain FTP with SFTP or FTPS for encrypted transfers.
- Keep your FTP server updated with the latest security patches.
2. SSH (Port 22) – Secure Shell
Attacks:
- Brute-force & Credential Stuffing: Attackers use automated tools to try common passwords or leaked credentials.
- Exploiting Old Vulnerabilities: Outdated SSH software may have known exploits (e.g., CVEs).
Defense:
- Disable password authentication; use SSH keys instead.
- Change the default SSH port to a non-standard number (security through obscurity).
- Use fail2ban or similar tools to block repeated failed login attempts.
- Regularly patch your SSH server.
- Allow SSH access only from trusted networks or via VPN.
3. Telnet (Port 23) – Unencrypted Remote Login
Attacks:
- Brute-force: Attackers try various credential combinations.
- Man-in-the-Middle (MitM): Data sent in plaintext can be intercepted.
- Sniffing: Passwords and commands are easily captured on the network.
Defense:
- Avoid Telnet. Use SSH instead.
- If you must use Telnet, restrict access to local networks and use strong, unique passwords.
- Monitor network traffic for unexpected Telnet activity.
4. SMTP (Port 25) – Simple Mail Transfer Protocol
Attacks:
- Spamming & Open Relay Abuse: Misconfigured servers relay spam.
- Phishing: Attackers send malicious emails that appear legitimate.
Defense:
- Disable open relay functionality.
- Implement SPF, DKIM, and DMARC to prevent email spoofing.
- Use email filtering and anti-spam solutions.
- Educate users about phishing risks.
5. DNS (Port 53) – Domain Name System
Attacks:
- DNS Amplification: Attackers exploit open resolvers for DDoS attacks.
- Cache Poisoning: Malicious responses trick DNS servers into saving false records.
- Tunneling: DNS is abused as a covert channel to exfiltrate data.
Defense:
- Disable recursion for external clients.
- Use DNSSEC to protect against spoofing and cache poisoning.
- Monitor DNS traffic for anomalies.
- Harden your DNS server with regular updates.
6. HTTP (Port 80) – Web Traffic (Unencrypted)
Attacks:
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages.
- SQL Injection: Malicious input alters database queries.
- Directory Traversal: Exploiting poor input validation to access sensitive files.
Defense:
- Validate and sanitize all user input.
- Implement Content Security Policy (CSP) for web applications.
- Use Web Application Firewalls (WAFs).
- Keep your web server and frameworks updated.
- Migrate to HTTPS to prevent eThe Most Common Network Port Attacks – And How to Defend Against Them
- By Jull3Haxor
- When it comes to cybersecurity, attackers rarely go in blind. They systematically scan for open ports—the digital doors and windows into your network. Some ports are more popular targets than others, simply because of the critical services running behind them. In this article, we break down the typical attacks seen on the most common ports and provide actionable defense strategies to help keep your systems secure.
- FTP (Port 21) – File Transfer Protocol
Attacks: - Brute-force & Anonymous Login: Attackers attempt to guess passwords or exploit misconfigurations allowing “anonymous” access, gaining entry without credentials.
- Directory Traversal: Malicious actors manipulate file paths to access directories and files outside the permitted scope, sometimes leading to full system compromise.
- Defense:
- Disable anonymous access unless absolutely necessary.
- Enforce strong, unique passwords and limit failed login attempts.
- Restrict FTP access to trusted IP addresses or internal networks.
- Replace plain FTP with SFTP or FTPS for encrypted transfers.
- Keep your FTP server updated with the latest security patches.
- SSH (Port 22) – Secure Shell
Attacks: - Brute-force & Credential Stuffing: Attackers use automated tools to try common passwords or leaked credentials.
- Exploiting Old Vulnerabilities: Outdated SSH software may have known exploits (e.g., CVEs).
- Defense:
- Disable password authentication; use SSH keys instead.
- Change the default SSH port to a non-standard number (security through obscurity).
- Use fail2ban or similar tools to block repeated failed login attempts.
- Regularly patch your SSH server.
- Allow SSH access only from trusted networks or via VPN.
- Telnet (Port 23) – Unencrypted Remote Login
Attacks: - Brute-force: Attackers try various credential combinations.
- Man-in-the-Middle (MitM): Data sent in plaintext can be intercepted.
- Sniffing: Passwords and commands are easily captured on the network.
- Defense:
- Avoid Telnet. Use SSH instead.
- If you must use Telnet, restrict access to local networks and use strong, unique passwords.
- Monitor network traffic for unexpected Telnet activity.
- SMTP (Port 25) – Simple Mail Transfer Protocol
Attacks: - Spamming & Open Relay Abuse: Misconfigured servers relay spam.
- Phishing: Attackers send malicious emails that appear legitimate.
- Defense:
- Disable open relay functionality.
- Implement SPF, DKIM, and DMARC to prevent email spoofing.
- Use email filtering and anti-spam solutions.
- Educate users about phishing risks.
- DNS (Port 53) – Domain Name System
Attacks: - DNS Amplification: Attackers exploit open resolvers for DDoS attacks.
- Cache Poisoning: Malicious responses trick DNS servers into saving false records.
- Tunneling: DNS is abused as a covert channel to exfiltrate data.
- Defense:
- Disable recursion for external clients.
- Use DNSSEC to protect against spoofing and cache poisoning.
- Monitor DNS traffic for anomalies.
- Harden your DNS server with regular updates.
- HTTP (Port 80) – Web Traffic (Unencrypted)
Attacks: - Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages.
- SQL Injection: Malicious input alters database queries.
- Directory Traversal: Exploiting poor input validation to access sensitive files.
- Defense:
- Validate and sanitize all user input.
- Implement Content Security Policy (CSP) for web applications.
- Use Web Application Firewalls (WAFs).
- Keep your web server and frameworks updated.
- Migrate to HTTPS to prevent eavesdropping.
- HTTPS (Port 443) – Web Traffic (Encrypted)
Attacks: - SSL/TLS Attacks: Outdated or misconfigured protocols can be exploited (e.g., Heartbleed).
- Phishing & Credential Harvesting: Malicious websites using HTTPS trick users into entering sensitive data.
- Defense:
- Disable insecure SSL/TLS versions (use TLS 1.2+).
- Use strong certificates from a trusted CA.
- Enable HSTS (HTTP Strict Transport Security).
- Monitor for phishing sites mimicking your domain.
- SMB (Port 445) – Server Message Block (File Sharing, Windows)
Attacks: - EternalBlue: A famous exploit used in ransomware attacks like WannaCry.
- Ransomware Spreading: Malware moves laterally through open SMB shares.
- Pass-the-Hash: Attackers reuse stolen password hashes to gain access.
- Defense:
- Disable SMBv1; use SMBv2/v3.
- Patch systems regularly (especially Windows).
- Restrict SMB access to local networks.
- Segment your network and monitor lateral movement.
- Use strong passwords and enable account lockout policies.
- RDP (Port 3389) – Remote Desktop Protocol
Attacks: - Brute-force: Attackers try to guess RDP credentials.
- BlueKeep: A critical RDP vulnerability allowing remote code execution.
- Defense:
- Limit RDP exposure to the internet—use VPN for remote access.
- Implement Network Level Authentication (NLA).
- Use account lockout and two-factor authentication.
- Patch Windows regularly.
- Monitor RDP logs for suspicious activity.
- Final Tips for Network Defense
- Close all unnecessary ports.
- Use a layered defense (firewalls, IDS/IPS, endpoint protection).
- Conduct regular vulnerability scans and penetration tests.
- Keep software and operating systems up to date.
- Train users on cybersecurity best practices.
- By understanding these common port-based attacks and applying strong, multi-layered defenses, you significantly reduce your risk of compromise—no matter the size of your network.
- Stay secure. Patch often. Hack the hackers!
- Did you enjoy this article? For more tips and deep dives, check out jull3.netavesdropping.
7. HTTPS (Port 443) – Web Traffic (Encrypted)
Attacks:
- SSL/TLS Attacks: Outdated or misconfigured protocols can be exploited (e.g., Heartbleed).
- Phishing & Credential Harvesting: Malicious websites using HTTPS trick users into entering sensitive data.
Defense:
- Disable insecure SSL/TLS versions (use TLS 1.2+).
- Use strong certificates from a trusted CA.
- Enable HSTS (HTTP Strict Transport Security).
- Monitor for phishing sites mimicking your domain.
8. SMB (Port 445) – Server Message Block (File Sharing, Windows)
Attacks:
- EternalBlue: A famous exploit used in ransomware attacks like WannaCry.
- Ransomware Spreading: Malware moves laterally through open SMB shares.
- Pass-the-Hash: Attackers reuse stolen password hashes to gain access.
Defense:
- Disable SMBv1; use SMBv2/v3.
- Patch systems regularly (especially Windows).
- Restrict SMB access to local networks.
- Segment your network and monitor lateral movement.
- Use strong passwords and enable account lockout policies.
9. RDP (Port 3389) – Remote Desktop Protocol
Attacks:
- Brute-force: Attackers try to guess RDP credentials.
- BlueKeep: A critical RDP vulnerability allowing remote code execution.
Defense:
- Limit RDP exposure to the internet—use VPN for remote access.
- Implement Network Level Authentication (NLA).
- Use account lockout and two-factor authentication.
- Patch Windows regularly.
- Monitor RDP logs for suspicious activity.
Final Tips for Network Defense
- Close all unnecessary ports.
- Use a layered defense (firewalls, IDS/IPS, endpoint protection).
- Conduct regular vulnerability scans and penetration tests.
- Keep software and operating systems up to date.
- Train users on cybersecurity best practices.
By understanding these common port-based attacks and applying strong, multi-layered defenses, you significantly reduce your risk of compromise—no matter the size of your network.
Stay secure. Patch often. Hack the hackers!