Researchers have disclosed a critical vulnerability in the Kigen eSIM (eUICC) remote management system, affecting mobile network infrastructure globally. The flaw could allow attackers to perform SIM profile swaps or hijacks via malicious over-the-air (OTA) messages — without physical access to the device.
The issue impacts GSMA-compliant eSIMs, raising serious concerns about remote control over subscriber identity and network access.
What Is Affected?
The vulnerability lies in the Kigen Subscription Manager Data Preparation+ (SM-DP+) platform, a key component that provisions eSIM profiles remotely over-the-air.
Attackers can potentially:
- Trick devices into accepting malicious profiles
- Hijack phone numbers or subscriber data
- Bypass authentication mechanisms during provisioning
- Cause denial-of-service or surveillance risk to mobile users
The issue affects eSIM infrastructure used by mobile carriers, device manufacturers, and IoT providers around the world.
Discovered by Security Researchers
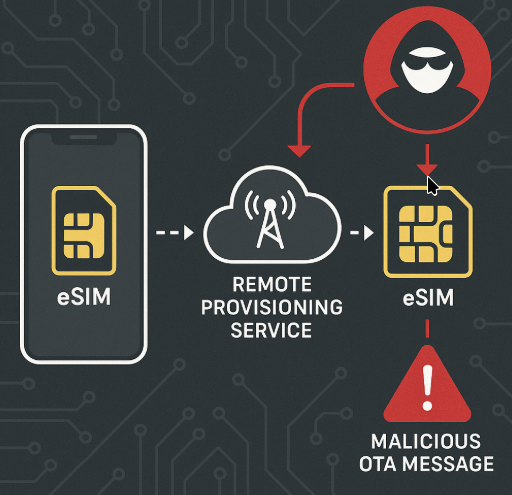
The flaw was identified by adaptiveMobile Security, who demonstrated how a malformed or maliciously crafted OTA message could trigger insecure profile handling, potentially allowing takeover of mobile identities at scale.
While Kigen has since issued updates and patches, details on CVE assignment are pending at the time of writing.
Kigen’s Response
Kigen acknowledged the vulnerability and has:
- Released security patches to affected telecom providers and partners
- Notified GSMA and ecosystem stakeholders
- Updated SM-DP+ and remote provisioning systems to mitigate risk
Customers are advised to ensure OTA provisioning services are updated and to audit profile delivery mechanisms.
Why This Matters
With the rising adoption of eSIMs in smartphones, wearables, and connected cars, the implications of this vulnerability are significant:
- Attacks can happen remotely, without touching the victim’s device
- SIM profile hijack enables interception of calls, messages, and data
- IoT fleets relying on Kigen’s eSIM stack are particularly vulnerable
Final Takeaway
This vulnerability highlights the need for end-to-end security in SIM provisioning infrastructure. As eSIM adoption grows, attacks will shift to backend systems — and that’s exactly what happened here.
Protecting your network now means securing both the SIM and the cloud behind it.
Source:
The Hacker News –
“eSIM Vulnerability in Kigen’s eUICC Module Could Allow SIM Hijacking Attacks”
🔗 https://thehackernews.com/2025/07/esim-vulnerability-in-kigens-euicc.html

